Android malware detection evasion and resilience techniques: some examples
Five examples and some suggestions
In a brief article on Symantec “Security Response” blog, Shaun Aimoto explains some techniques used by malware creators to evade security apps analysis.
Packing

Android packers are able to encrypt an original classes.dex file, use an ELF binary to decrypt the dex file to memory at runtime, and then execute via DexclassLoader, changing structure and flow of the APK file: a bit more complicated than obfuscation techniques such as ProGuard and DexGuard.
The packer engine applies various transformations to the input JAR file, making the pack stream highly compressible by a compressor such as gzip or zip. An instance of the engine can be obtained using newPacker(). The high degree of compression is achieved by using a number of techniques described in the JSR 200 specification. Some of the techniques are sorting, re-ordering and co-location of the constant pool.
(https://developer.android.com/reference/java/util/jar/Pack200.Packer.html)
MultiDex apps

Android applications contain executable code contained within Dalvik Executable (DEX) files: a typical Android app has a single DEX file and standard malware detection focuses on this file.
However some Android malware splits its payload between two DEX files and this step can serve as a cheap evasion technique against static analysis.
For more information about Multidex, refer to official documentation.
Instant Run-based malware
Instant Run allows developers to quickly deploy updates to a debug application by pushing an update .zip file into the application.
However this approach can only be used on Android Lollipop and later SDK levels and it applies only to debug-version apps that are installed by sideloading.
From documentation:
Introduced in Android Studio 2.0, Instant Run is a behavior for the Run and Debug commands that significantly reduces the time between updates to your app. Although your first build may take longer to complete, Instant Run pushes subsequent updates to your app without building a new APK, so changes are visible much more quickly.
Instant Run is supported only when you deploy the debug build variant, use Android Plugin for Gradle version 2.0.0 or higher, and set minSdkVersion to 15 or higher in your app’s module-level build.gradle file. For the best performance, set minSdkVersion to 21 or higher.
Malformed manifest files
This method can trick and hang up static scanners using strange values in the app manifest file (AndroidManifest.xml) such as inaccurate size values and magic values in headers, junk data into the string pool and at the end of files, or mismatching XML namespaces.
Using chattr to lock malware into the system
Malware that is able to gain root privileges on a device can be particularly difficult to remove.
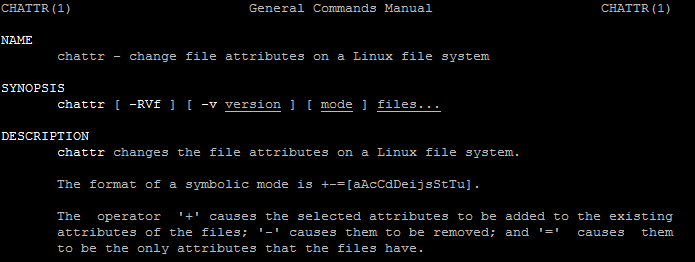
This technique involves the chattr Linux command, which, when used on a file, can prevent it from being deleted even with root privileges.
The chattr command is a part of BusyBox package, and can be packed (encrypted) into the app and used for lock the malicious APK into the system folder.
Syntax of chattr
# chattr [operator] [flags] [filename]
The operator ‘+’ causes the selected attributes to be added to the existing attributes of the files; ‘-’ causes them to be removed; and ‘=’ causes them to be the only attributes that the files have.
The letters ‘acdeijstuADST’ select the new attributes for the files:
- a: append only
- c: compressed
- d: no dump
- e: extent format
- i: immutable
- j: data journalling
- s: secure deletion
- t: no tail-merging
- u: undeletable
- A: no atime updates
- D: synchronous directory updates
- S: synchronous updates
- T: top of directory hierarchy
for example, the command
chattr +1 /data/app/com.malicious.app.apk
makes the file com.malicious.app.apk “immutable”, so that even root can’t remove it.
Mitigations?
The post on Symantec’s blog ends with some suggestion:
- Keep your software up to date
- Only install apps from trusted sources such as Google Play
- Pay close attention to the permissions that apps request
- Install a suitable mobile security app, such as Norton, to protect your device and data (product placement! :-) )
- Make frequent backups of important data