Domain Fronting in a nutshell
What is Domain Fronting? How it works? How can be used to evade internet censorship?
Recently both Google and Amazon announced a change to its own infrastructure in order to avoid the use of domain fronting, the exploitation of a content delivery network’s architecture to conceal the actual destination of encrypted Internet traffic.
A lot of privacy related application uses this techniques to evade censorship, like Signal, Tor-to-Web proxies, the GreatFire service to bypass China's Great Firewall.
Furthermore lots of VPN providers uses Domain Fronting to hide their servers' real locations.
But, what is Domain Fronting, how it works and why providers starting block this kind of traffic?
A brief description
Domain Fronting is a masquerading technique that is typically used to circumvent Internet censorship by making traffic look like it’s associated with a web domain that isn’t restricted.
Usually, domain fronting relies on content delivery networks (CDN) that host multiple domains.
A single CDN may host thousands of different domains, even if the CDN itself is operated by a single company like Akamai, Amazon, Microsoft Azure, or CloudFlare.
Because of the nature of CDNs, mobile providers and censorship proxies cannot simply block them, as that would unintentionally block many major websites and services.
For example, facebook.com typically serves content from IP addresses owned by Facebook, but some contents are also served from domains like xxxx.akamai.net.
Using an application like Psiphon, the traffic can be routed to a CDN server: when traffic reaches the CDN, it’s re-routed through a domain fronting server (in this case the psiphon’s server) to its end destination.
This re-routing process effectively masks the user’s traffic and makes it appear like all Internet traffic is coming from a legitimate website or application hosted on the CDN.
Through domain fronting, a user could potentially route all of his internet traffic through psiphon’s servers and make it look identical to authorized traffic.
But despite the technique's use with legitimate apps trying to skirt government-based bans, the domain fronting had also started to become popular on the cybercrime scene, used to disguise the locations of command-and-control servers: the russian cyber-espionage group APT29 uses this technique with TOR for its malware operations.
[caption id="attachment_3118" align="alignnone" width="1170"]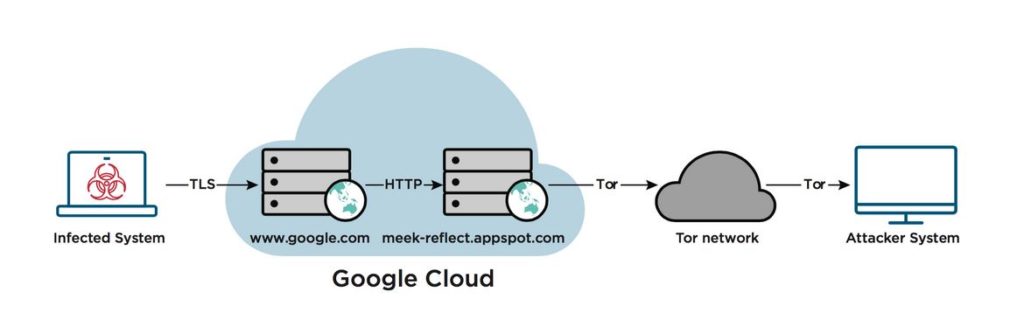 source: https://www.fireeye.com/blog/threat-research/2017/03/apt29_domain_frontin.html[/caption]
source: https://www.fireeye.com/blog/threat-research/2017/03/apt29_domain_frontin.html[/caption]
Finally, this technique can also used to perform a zero-rate fraud on mobile networks: for example, a fraudster could disguise all of their Internet traffic to look like Facebook, and thereby take advantage of a zero-rated Facebook plan.
How it works?
Now let's try to explain a real use case of Domain Fronting, involving a final user that try to avoid internet censorship from his mobile phone.
With normal Internet behavior, when a user visits a website, they send three domain name requests, sent over the DNS, TLS (in the SNI field) and HTTP protocols.
Generally, the three protocols include the same domain name to avoid confusion when searching for the location of the requested content: however, when a user performs a domain fronting using an app like Psiphon, a different domain name is included in the HTTPS request (think of it as a virtual host in your Apache configuration).
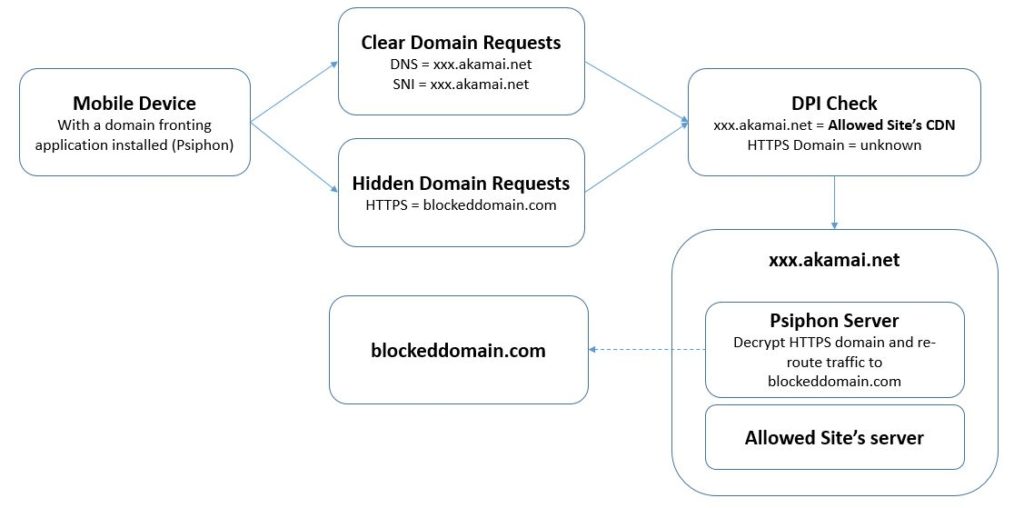
Since the HTTPS domain name is encrypted, censorship solutions doesn’t see that the HTTPS domain name doesn’t match with the DNS and SNI fields, and only considers DNS and SNI when reviewing the traffic.
This partial scan is unable to see the true nature of the Internet traffic and instead believes that the user is accessing legitimate content hosted on a CDN.
Once inside the CDN, the HTTPS domain name is decrypted by a domain fronting server (the psiphon’s server, hosted on the same CDN) and the traffic is re-routed to the hidden destination.
Below an interesting video by Vincent Yiu that explains how to perform a domain fronting on Amazon Cloudfront (after the Amazon ban this technique cannot be longer applied) :
[embed]https://www.youtube.com/watch?v=zSBnM2HcRTw[/embed]
What is Psiphon?
Psiphon is a circumvention tool that utilizes VPN, SSH and HTTP proxies to provide an uncensored access to Internet content, helping people in freedom-restricted countries around the world safely access censored websites.
https://www.youtube.com/watch?v=jTwmcwlkGi0
Psiphon is an open-source project, developed in Go.
So, every user can deploy his own psiphon server using the sourcecode on GitHub repository.
References and further readings
-
- Amazon blocks domain fronting, threatens to shut down Signal’s account
- Google disables “domain fronting” capability used to evade censors
- Google and Amazon put an end to censorship-dodging domain fronting
- Psiphon sourcecode repository
- Psiphon Home Page
- Enhanced Domain Protections for Amazon CloudFront Requests
- Amazon threatens to suspend Signal's AWS account over censorship circumvention
- APT29 Domain Fronting With TOR
- Blocking-resistant communication through domain fronting