Malware VM detection techniques evolving: an analysis of GravityRAT
The malware detects virtualized environments by taking infected machines' CPU temperature.
When a malware infect a system, one of the next steps that it performs is gain persistence, a mandatory key to ensure the resilience of (for example) the connection with a C&C.
I've already written some posta about the techniques used by malware in order to hiding in the target system and mantain the persistence, however every day a new method come out in the wild.
Recently, Cisco Talos threat research division has performed an interesting analysis of GravityRAT, a malware has largely stayed under the radar for at least two years, and allows adversaries to perform reconnaissance on affected machines, exfiltrate files, and execute arbitrary code.
GravityRAT infects computers using a Microsoft Office documents containing a small, embedded malicious macro, that performs three steps:
- copies the active document in a temporary directory and renames it as a ZIP archive
- decompresses the .zip file and extracts the malicious executable inside it
- creates a scheduled task to execute this file each day
But the intersting feature of GravityRAT is the set of techniques which it uses to dodge virtual environments that are typically used to create sandboxes for malware analysis.
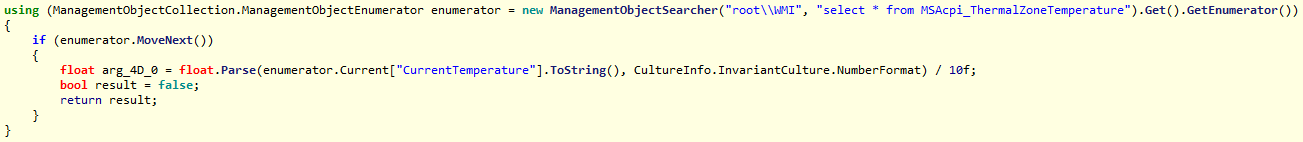
In its analysis, Talos identify seven ways the malware attempts to check if the compromised system is a virtual machine (search of hypervisor tools, check bios version, number of cores and other standart techniques), but the most unusual is by employing a WMI request to check the current CPU temperature.
The sixth technique checks the current CPU temperature of the system (the MSAcpi_ThermalZoneTemperature entry).
This tactic often works because most hypervisors, including Hyper-V, VMWare Fusion, VirtualBox, KVM and XENs, do not support the temperature check function: therefore, the response from the WMI request is an error message that allows the malware to identify the sandbox.
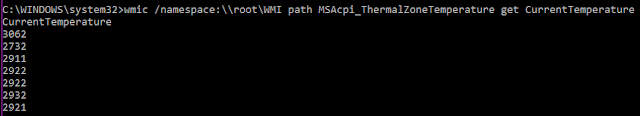
For example, here is the output of the query on a physical machine, that returns the temperature of 7 thermal zones:
And here is the output on a Virtual Machine executed by Hyper-V on the same hardware:
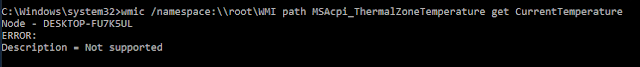
From our tests and the feedback from several researchers, this monitoring is not supported on Hyper-V, VMWare Fusion, VirtualBox, KVM and XEN. It's important to notice that several recent physical systems do not support it (a researcher reported some Lenovo and Dell hosts did not support this). It means that GravityRAT will consider this physical machine as VMs.
Importantly to note this check is not foolproof as we have identified physical hosts which do not report back the temperature, however, it should also be considered a check that is identifying a lot of virtual environments.
This is particularly important due to the amount of sandboxing & malware detonation being carried out within virtual environments by researchers.
References and further reading
- GravityRAT - The Two-Year Evolution Of An APT Targeting India
- Malware hiding and evasion techniques
- Windows Command Line cheatsheet (part 2): WMIC