SurfingAttack: manipulating voice assistant devices with ultrasonic waves
A research team has recently discovered a new attack method that enables remote users to interact with voice-controlled device using ultrasonic waves transmitted through (for example) the surface on which is placed the target device.
The attack, dubbed "SurfingAttack" [1] may allows a malicious user to hijack a mobile SMS passcode, making ghost fraud calls without owners’ knowledge, etc.
The research team
- Qiben Yan at SEIT Lab, Michigan State University
- Kehai Liu at Chinese Academy of Sciences
- Qin Zhou at University of Nebraska-Lincoin
- Hanqing Guo at SEIT Lab, Michigan State University
- Ning Zhang at Washington University in St. Louis
Is not new
Other research have in the past revealed how ultrasonic waves that are not audible to the human hearing can be used to control different voice assistant devices: in 2017, a similar attack dubbed DolphinAttack was disclosed.
However, DolphinAttack had a couple of conditions :
- There must be a clear line of sight between the device and the ultrasound waves emitter.
- The distance should be short between the two.
How does attack works?
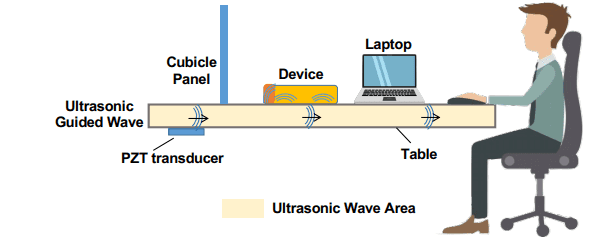
To launch a SurfingAttack the attackers not required to stay in line-of-sight, it can be launched secretly without alerting users in physical proximity.
Researchers also said that the attack is Omni-directional, and the success of the attack is not impacted by objects on a busy tabletop.
The attack leverages the non-linearity of the microphone circuits to inject inaudible commands to these systems: audio capturing hardware in the voice-controllable systems generally includes a micro-electromechanical system which converts a mechanical vibration to a digital signal, and the attack exploit this feature.
Which are the vulnerable devices?
According to the paper [2]:
| Manufacturer | Model | OS |
| Pixel | Android 10 | |
| Pixel 2 | Android 10 | |
| Pixel 3 | Android 10 | |
| Moto | G5 | Android 7.0 |
| Moto | Z4 | Android 9.0 |
| Samsung | Galaxy S7 | Android 7.0 |
| Samsung | Galaxy S9 | Android 9.0 |
| Samsung | Galaxy Note 10+ | Android 10 |
| Xiaomi | Mi 5 | Android 8.0 |
| Xiaomi | Mi 8 | Android 9.0 |
| Xiaomi | Mi 8 Lite | Android 9.0 |
| Huawei | Honor View 10 | Android 9.0 |
| Huawei | Mate 9 | Android 8.0 |
| Apple | iPhone 5 | iOS 10.0.3 |
| Apple | iPhone 5s | iOS 12.1.2 |
| Apple | iPhone 6+ | iOS 11 |
| Apple | iPhone X | iOS 12.4.1 |
Are there some countermeasure?
In the paper, researchers suggests some mitigations (In my opinion, the second one is the easiest to apply):
Hardware Layout Enhancement
One prerequisite for the success of the attack is that the ultrasonic voice commands can propagate along the device body to the microphones. Thus, the layout of microphone could be enhanced and redesigned to damp or suppress any acoustic vibration whose frequencies are in the ultrasound range.
Interlayer-based Defense
One effective but simple defense mechanism of SurfingAttack is to place the device on a soft woven fabric or a multilayers term (the peva & non-woven two layers tablecloth in Table VIII) to increase the impedance mismatch.
Software-based Defense
An ideal software-based defense approach should identify and reject received voice commands