Some thoughts about detectability and feasibility of mobile eavesdropping on smartphones
A research presented in 2019 by Jacob Leon Kröger and Philip Raschke, during the 33rd Annual IFIP WG 11.3 Conference, analyze technical and economical feasibility of eavesdropping on modern smartphones.
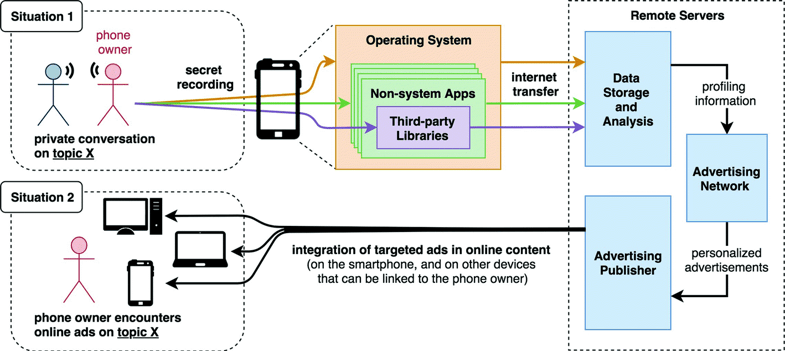
The study’s findings [1] suggest that eavesdropping activity would not be detected by current security mechanisms. Not only microphones, but also seemingly harmless motion sensors could be a potential eavesdropping channel in smartphones.
Microphone-Based Eavesdropping
Modern smartphones have the capability to tape any sort of ambient sound through built-in microphones, including private conversations, and to transmit sensitive data, such as the recording itself or information extracted from recorded speech, to remote servers over the Internet. Mobile apps installed on a phone could exploit these capabilities for secret eavesdropping.
Before an app can access microphones in Android and iOS devices, permission has to be granted by the user. However, people tend to accept such requests blindly if they are interested in an app’s functionality.
A survey of 308 Android users found that only 17% of respondents paid attention to permissions during app installation, and no more than 3% of the participants correctly answered the related comprehension questions.
Motion Sensor-Based Eavesdropping
Adversaries might be able to eavesdrop on conversations through cell phones without accessing the microphone. Studies have shown that smartphone motion sensors – more specifically, accelerometers and gyroscopes – can be sensitive enough to pick up sound vibrations and possibly even reconstruct speech signals.
Using only smartphone gyroscopes, researchers from Israel’s defense technology group Rafael and Stanford University were able to capture acoustic signals rich enough to identify a speaker’s gender, distinguish between different speakers and, to some extent, track what was being said. In a similar experiment, Zhang et al. demonstrated the feasibility of inferring spoken words from smartphone accelerometer readings in real-time, even in the presence of ambient noise and user mobility.
According to their evaluation, the achieved accuracies were comparable to microphone-based hotword detection applications such as Samsung S Voice and Google Now.
I suggest to read the whole research [1], that contains more information about the real feasibility of this kind of attack, and a good overview of available mitigations, such as:
App Inspections Conducted by Ecosystem Providers
Both iOS and Android apply a combination of static, dynamic and manual analysis to scan new and existing apps on their respective app market for potential security threats and to ensure that they operate as advertised
or
App Inspections Conducted by the Research Community
In addition to the checks conducted by Google and Apple, mobile apps are being reviewed by a broad community of security and privacy researchers. A wide and constantly expanding range of manual and automated methods is applied for this purpose.