146 new security vulnerabilities discovered in various Android versions
Researchers by security firm Kryptowire have discovered and revealed 146 vulnerabilities in various version of Android.
The vulnerabilities were found by scanning the phones of 29 different Android models using a set of custom automated tools [1].
The discovery workflow
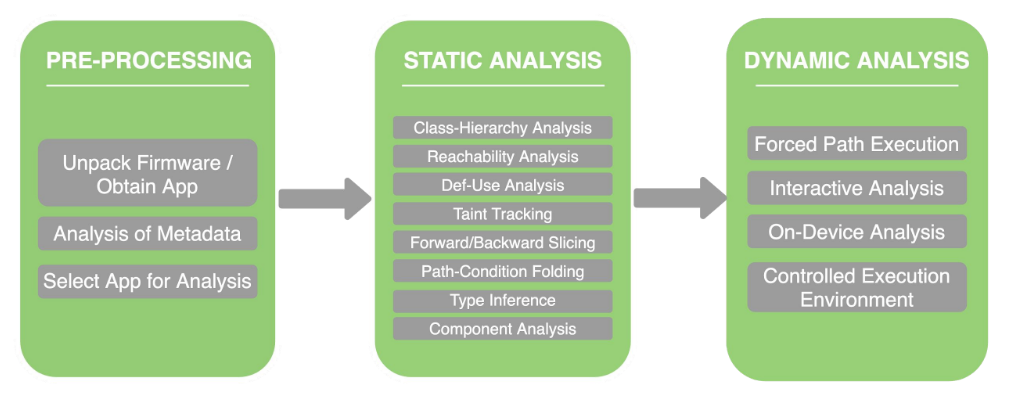
According with a brief paper published by Kryptowire [2], the analysis workflow is composed by 3 steps:
Mobile Apps & Firmware Collection
Mobile Apps and Firmware images are collected and processed by the App analysis system using a cloud or on-premise appliance.
Vulnerabilities Discovered
The automated system reports vulnerabilities with the type (e.g. command execution) and all necessary data to generate a proof of concept.
Exploits Generated
An analyst leverages the output of the automated system to validate and generate Proof of Concept exploits. The POCs can be tested and validated in live environments.
The analysis focused on a specific group of vulnerabilities:
- PII leakage
- Command execution
- Record audio
- Record screen
- Capture screenshot
- SMS sending
- Modification of system properties
- App installation
- Sending AT commands
- Logcat leakage
- Factory reset
- Dynamic code loading and execution
- Modification of wireless settings
- Others
The point of view of Bruce Schneier
The point of view of Bruce Schneier [3] (a famous cybersecurity specialist) is, in my view, really interesting (despite the scent of conspiracy):
There is no indication that any of these vulnerabilities were put there on purpose, although it is reasonable to assume that other organizations do this same sort of scanning and use the findings for attack. And since they're firmware bugs, in many cases there is no ability to patch them.
I see this as yet another demonstration of how hard supply chain security is.