Full Disk Encryption: tools and setup suggestion for personal data protection
In order to avoid sourveillance, privacy invasion or information theft you must be sure that the data on your devices are secure, and the only way to do that in this day and age is to make sure they are full disk encrypted.
Full Disk Encryption refers to taking a hard drive inside of a device and encrypting it as a whole so that all the files it has are converted into an unreadable form (encrypted) and not accessible without the password to decrypt them.
Today i'd like to share an overview on major full encryption solutions for most known OS/devices.
OsX
FileVault2
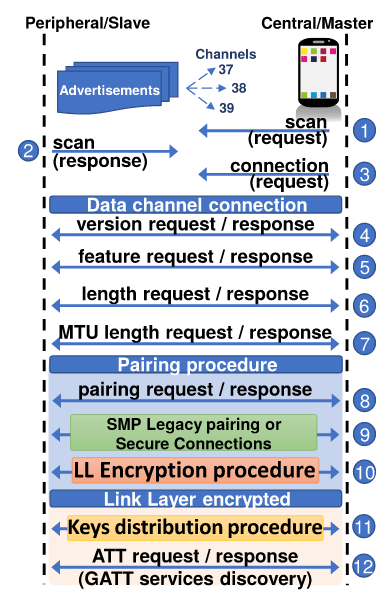
Native to all versions of Lion and up, FileVault2 is the advancement on the original FileVault that only encrypted the home folder.
It uses 128bit AES in XTS mode to encrypt the disk and is highly suggested when setting up a new computer that has Yosemite or higher.
Good strategy here on part of Apple to include a dedicated section about it in the initial computer setup when you first start OSX.
When you set up FileVault2 for the first time, it requires you to have a password on the current administrator account and uses a random number generator (with about 320 bits of randomness available after first boot) to create a recovery key.
Based on some findings in this paper, FileVault2 uses PBKDF2 x SHA256 and 41,000 iterations on the password.
This works to prevent bruteforcing the password due to the delay in checking the hashed password with the one stored on the system.
There also doesn’t appear to be a limit to the password length so one could in theory create one 100 characters long without any issues other than delay before unencrypting.
It is unknown, but unlikely, if a backdoor has been implemented by Apple in FileVault2.
The full disckencryption can be enabled with this steps:
- Choose Apple menu > System Preferences, then click Security & Privacy.
- Click the FileVault tab.
- Click , then enter an administrator name and password.
- Click Turn On FileVault.
Linux
LUKS
Short for Linux Unified Key Setup, LUKS is the full disk encryption solution used by many Linux/GNU based operating systems.
Typically, it uses AES 256-bit encryption in CBC mode with SHA256 for hashing but that can be edited if needed to run other modes like XTS and decreasing the key size of the AES algorithm to 128-bit.
Like FileVault2 for OSX, LUKS has no character limit for the passwords/passphrases and I have tested this with a 212-character passphrase consisting of letters, numbers, spaces, and symbols.
The iteration count for LUKS is specified by the CPU power of the machine. For slower computers, this may be lower than wanted so it can be specified with the cryptsetup command.
The command would be:
cryptsetup luksFormat -i 15000 <target device>
I would recommend experienced users setting the value at no less than 20,000.
LUKS is also fully open source that along with its consistent use within Linux distributions makes it a very trusted choice for FDE.
The procedure for enabling full disk encryption with LUKS is not simple, especially on a system already installed.
You can refer to this tutorial on nixCraft: How To: Linux Hard Disk Encryption With LUKS
Windows
VeraCrypt

When TrueCrypt died back in 2014, Mounir Idrassi starts a fork of the project called VeraCrypt.
It is considered to be the official upgrade to TrueCrypt by many as it is open source, and had a code audit completed in October of 2016 (see: https://ostif.org/the-veracrypt-audit-results/).
VeraCrypt implements a lot of cryptographic improvements over TrueCrypt, has also made some graphical and usability improvements, like adding a randomness meter to the “move your mouse screen” to display the random entropy you are acquiring.
As of October 2016, VeraCrypt has implemented some new algorithms for both encryption and hashing which is a positive move forward.
Camelia and Kuznyechik were added as encryption algorithms, but stand-alone and are not able to be paired like the original three, and Streebog has been added as a hash algorithm.
Moving forward, it would be nice to see an algorithm for encryption with Camelia and Serpent as a team.
That way, we are able to get the added security of two encryption algorithms in cascading fashion, without having to rely on AES.
VeraCrypt Encryption Algorithms:
- Serpent
- AES
- TwoFish
- Camellia
- Kuznyechik
VeraCrypt Hash Algorithms:
- SHA-256
- SHA-512
- Whirlpool
- RIPMD-160
- Streebog
The procedure for enabling full disk encryption with VeraCrypt is more simple than Linux/LUKS, but there are still a lot of steps.
I suggest to refer to this tutorial on HowToGeek: How to Encrypt Your Windows System Drive With VeraCrypt
iOS Devices

Apple mobile devices running anything above version 8.0 are protected with Full-Device Encryption by default known as “Data Protection” in your Passcode settings.
However, there is a big leap up from the 5C to the 5S and all devices from here on out that have TouchID.
The listed devices above 5S (6, 6S, 7, etc), currently offers the best encryption.
This devices have an hardware chip inside called Secure Enclave that manages all encryption and the delays in between password attempts.
All versions of iOS above 8 employ 256-bit AES full-device encryption in a unique way that protects all data past the lock screen.
This data on the above listed devices is secured using an ephemeral key generated on boot that is entangled with your devices unique UUID to do the encryption. User passcode protects this key.
The device level encryption that is deemed to be very secure (but not 100% yet), Apple pushed out properly encrypted iCloud backups in 9.3 that use the device’s passcode to encrypt the backup.
Prior to this, Apple was able to give out iCloud backups when presented with a warrant and a user really couldn’t be deemed completely secure unless they disabled these backups on the device.
Android devices
The built-in Android full-disk encryption is based on dm-crypt, which is a kernel feature that works at the block device layer: encryption works with eMMC and similar flash devices that present themselves to the kernel as block devices.
The encryption algorithm is 128 Advanced Encryption Standard (AES) with cipher-block chaining (CBC) and ESSIV:SHA256.
The master key is encrypted with 128-bit AES via calls to the OpenSSL library.
The encryption can be enabled with few simple steps:
- Enter the Settings menu
- Under "Personal", tap Location & Security, Security & Location, Security, or Security & Screen Lock
- Click Encrypt device, Encryption, Data Encryption, or Encryption & Credentials.
- Tap Encrypt device/phone/tablet. If you see a checkbox for Device Data, tap to select it, and if you see a checkbox for Storage (Encrypts files you save to your memory card and internal storage), tap to select it.
- Start encryption process.
Schedule an hour or more for the encryption process. If you interrupt it, you will lose some or all of your data.
So, charge the battery or plug in your device.