Security analysis of Telegram Messenger
Do you need a secure and private messenger? You shouldn't be use Telegram!
In the past, I've already written about security laks of major messenger systems [1].
So, today I'd like to share some interesting highlight from a post by HackerFactor [2]: a good security analysis of desktop app of Telegram messenger.
Network Security
Telegram encrypts the communication, but it is trivial to detect the traffic, block access, and identify the offending user;
Telegram uses strong encryption between the client's device and their server. Normally, I would give them high marks for this. However, they operate as a trojan protocol.
HTTPS is a well-defined protocol. It is HTTP over TLS and it uses TCP on port 443. Anything using port 443/tcp should be speaking TLS. Anything using 443/tcp without TLS is a trojan protocol: it uses a well-known port but doesn't speak the well-known protocol. Telegram uses their own encryption protocol over 443/tcp.
For example, companies may spies "private" chats of employees:
...they can use a stateful packet inspector. If they see any traffic on 443/tcp where the first data packet lacks the TLS header, then they know it's a trojan protocol and they can kill the connection (e.g., TCP RST or silently drop). These companies can also trivially find the IP address of the internal employee who is violating the corporate policy.
Server Storage and Encryption
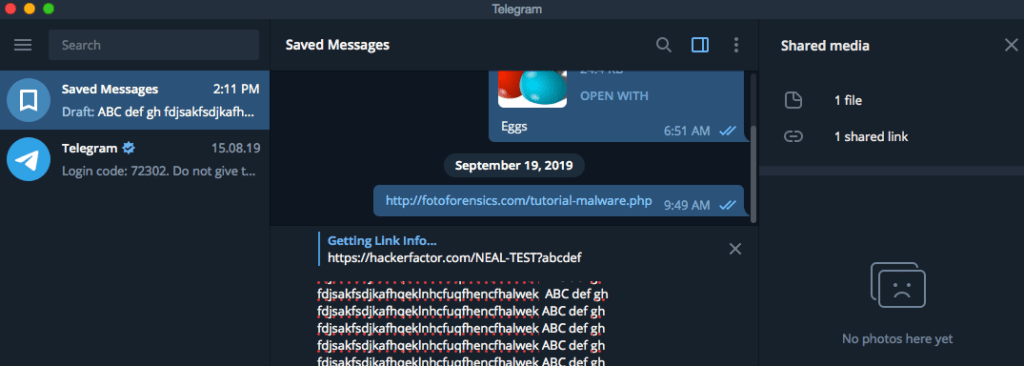
Using Wireshark, researcher spot some interesting data transfers:
While I was typing, there would be no network activity. But if I paused while typing, then after 3-5 seconds, there would be a transfer from my Telegram client to the server. They seem to be transferring my text to their server. I though that this could be related to saving as a draft message, except that drafts appear to be saved on the local file system (more about that in the next section).
But a more interesting behaviour happen when users types a URL:
But it gets worse: If I type a URL, then during the pause there would be a brief pop-up that says "Getting Link Info...". Since I own my own web server, I added in a URL to a non-existing web page on my site. This allowed me to see the request in the web logs:
149.154.161.14 - - [09/Mar/2020:14:10:22 -0600] "GET /NEAL-TEST HTTP/1.1" 301 5 "-" "TelegramBot (like TwitterBot)" 149.154.161.13 - - [09/Mar/2020:14:10:24 -0600] "GET /NEAL-TEST?abcd HTTP/1.1" 301 5 "-" "TelegramBot (like TwitterBot)" 149.154.161.5 - - [09/Mar/2020:14:10:47 -0600] "GET /NEAL-TEST?abcde HTTP/1.1" 301 5 "-" "TelegramBot (like TwitterBot)" 149.154.161.2 - - [09/Mar/2020:14:11:53 -0600] "GET /NEAL-TEST?abcdef HTTP/1.1" 301 5 "-" "TelegramBot (like TwitterBot)"
These logs show the few seconds of pause and the Telegram server (149.154.160.0/20) retrieving the web page. So the URL that I was typing in my draft message (never sent by me since I was still composing the message) went from my Telegram client to the Telegram servers. Moreover, the server did a 'GET' and not a 'HEAD' request. ('HEAD' is for checking if a URL exists. 'GET' can cause actions and receives full web page results.)
This tells me that the data is transferred using encryption to their servers. However, then the server decrypts it and accesses the raw, unencrypted text.
Local Storage and Encryption
At this point, researcher focused on local log files written by the app:
On my local computer, Telegram stores a bunch of encrypted files. (I'm using a Mac and the files are in "~/Library/Containers/org.telegram.desktop/Data/Library/Application Support/Telegram Desktop/tdata".) They look like binary files and most of them start with "TDEF", denoting a Telegram Data Encrypted File [3].
The local directory also contains a "log.txt", which records in plain text the last time I ran Telegram. (This can be really useful to a forensic examiner if you use a backup system and have a history of these log files.)
So, files are encrypted. However, there are some issues:
Since the data is stored locally, the question becomes: how easy is it to decrypt? As it turns out, it's not too difficult since the encryption keys are nearby. Over at github, there's a tool called telegram-desktop-decrypt [4] that can decode text, images, and videos from the local files. There is also TelegramStorageParser [5] and other tools for decrypting the local files. In other words, the data may be encrypted but it is readily decipherable by anyone with access to the local files.
Over at Medium, there's an interesting observation from 2018. According to Evgeniy Lazarev [6], Telegram has a setting to remove cache files but doesn't obey the setting. You may think that you are deleting old files from the local file system, but you're not really. Fortunately, he provided a quick script for forcefully deleting these files. (I haven't tested whether this is still the case since my cache isn't very large, but I do have an old cache that it doesn't seem to delete.) This means that your computer may store chats, images, and other sensitive content going back years.
Moral of the story
Pretty simple: If you need a secure messenger, do not use telegram!
These "secure" chat tools are supposed to allow you to send encrypted messages. Most of them work as expected, even if they have some quirks. However, Telegram appears to receive, store, and cache the unencrypted messages on their servers. They access confidential URLs and cache URL results. Moreover, they store "encrypted" files on the local device that are readily decipherable.
Then again, what do you expect from a "secure" chat platform that is funded [7] by a Russian oligarch and a former Russian cabinet minister? Seriously: Don't use Telegram.
References
- Why WhatsApp (and Telegram) messages are not really private?
- Not So Secret Messages
- Telegram Data Encrypted File
- telegram-desktop-decrypt
- TelegramStorageParser
- Telegram on Mac OS takes no care about your disk storage and feels great about it
- Russian Oligarch, Ex-Cabinet Minister Invested in Telegram’s ICO, Court Filing Says