Digital Forensic Basics: an analysis methodology flow chart
Data extraction, data acquisition, data analysis? Let's try to make it a little clearer!
Let's start from the beginning...
In the early 1980s, when personal computers began to be more accessible to consumers, however, increasing their use in criminal activities, the field of forensic information technology was born: a relatively young compared to other forensic sciences.
Although digital forensic is used in many judicial proceedings as one of the main means of investigation linked to various crimes, it is not always possible to fully understand what the term computer forensic means and what are the techniques involved. In particular, there is often a lack of clarity regarding the distinction between data extraction and data analysis.
A little, graphical help...
The Cybercrime Lab in the Computer Crime and Intellectual Property Section (CCIPS) has developed an interesting flow chart that describes in detail the digital forensic analysis methodology, clarifying the various phases of the forensic analysis process:
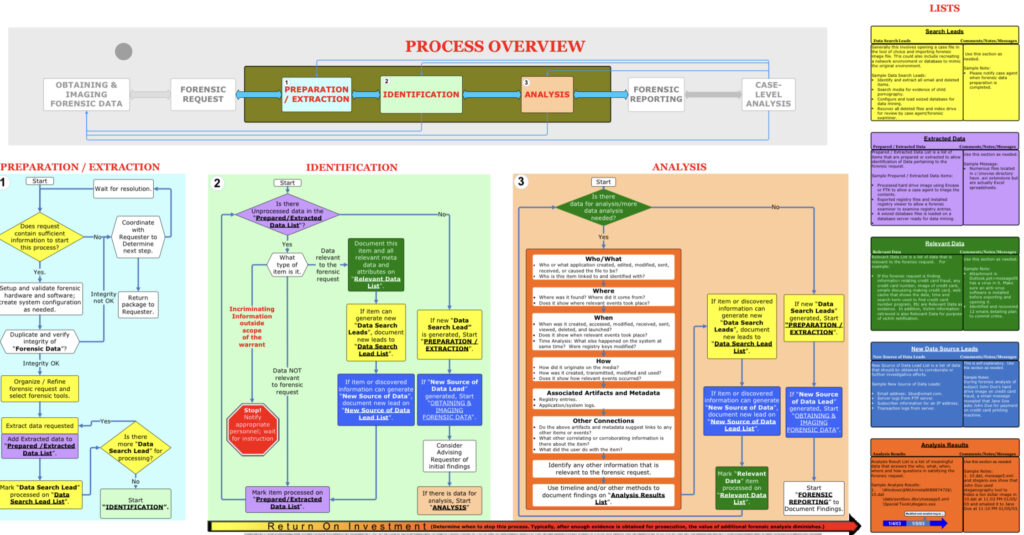
This flow chart is the result of the collaboration of several DFIR experts operating in various American federal agencies, and it is a valid guide during the investigation phases.