Windows registry Transaction Logs in forensic analysis
During forensic anaysis, Windows registry data can be useful to discover malicious activity and to determine if and what data may have been stolen from a network.
Many different types of data are present in the registry that can provide evidence of program execution, application settings, malware persistence, and other valuable artifacts.
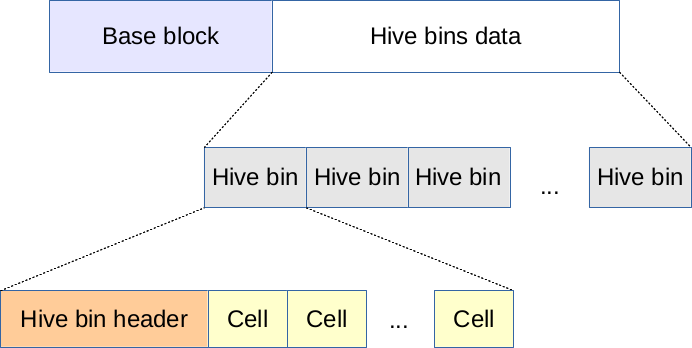
The Windows registry is stored in a collection of hive files: hives are binary files containing a simple filesystem with a set of cells used to store keys, values, data, and related metadata, written in 4KB pages [1].
Furthermore, in order to maximize registry reliability, since Windows 2000 the OS can use transaction logs when performing writes to registry files. That logs act as journals that store data being written to the registry before it is written to hive files: they are used when registry hives cannot directly be written due to locking or corruption.
The amount of data that can be recovered from this type of artefacts depends on registry activity: likewise filesystem carving process, registry-heavy operations, such as system updates, can significantly reduce the recoverable data.
How to recover data from Registry Transaction Logs?
In my opinion, the recovery of this kind of data can be accomplished just using the correct registry file analysis tool: usually, i use regipy [2], a python tool developed by Martin Korman:
Regipy is a python library for parsing offline registry hives. regipy has a lot of capabilities:
Use as a library:
- Recurse over the registry hive, from root or a given path and get all subkeys and values
- Read specific subkeys and values
- Apply transaction logs on a registry hiveCommand Line Tools
- Dump an entire registry hive to json
- Apply transaction logs on a registry hive
- Compare registry hives
- Execute plugins from a robust plugin system (i.e: amcache, shimcache, extract computer name...)
Regipy usage
First, install the tool:
pip install regipy
Then use it to recover a registry hive, using transaction logs:
registry-transaction-logs NTUSER.DAT -p ntuser.dat.log1 -s ntuser.dat.log2 -o recovered_NTUSER.dat