Be careful! A Windows flaw lets Zoom leak network credentials and run code remotely
Researcher have found a security issue in the Windows client of the popular video conferencing service that can be used for limited remote code execution and, worse, to capture and replay security tokens to access network resources.
The app has vulnerability [1] in handling of Uniform Resource Identifier paths, which can result in Universal Naming Convention (UNC) [2] injection.
The vulnerability was found by Matthew Hickey and reported to zoom:
Currently, a patch in not available.
How it works?
When sending a chat message, any URLs that are sent are converted into hyperlinks so that other members can click on them to open a web page in their default browser.
The problem is that the Zoom client will convert Windows networking UNC paths into a clickable link in the chat messages as well.
If a user clicks on a UNC path link, Windows will attempt to connect to the remote site using the SMB file-sharing protocol to open the remote file.
When doing this, by default Windows will send the user's login name and their NTLM password hash, which can be cracked using free tools like Hashcat to dehash, or reveal, the user's password.
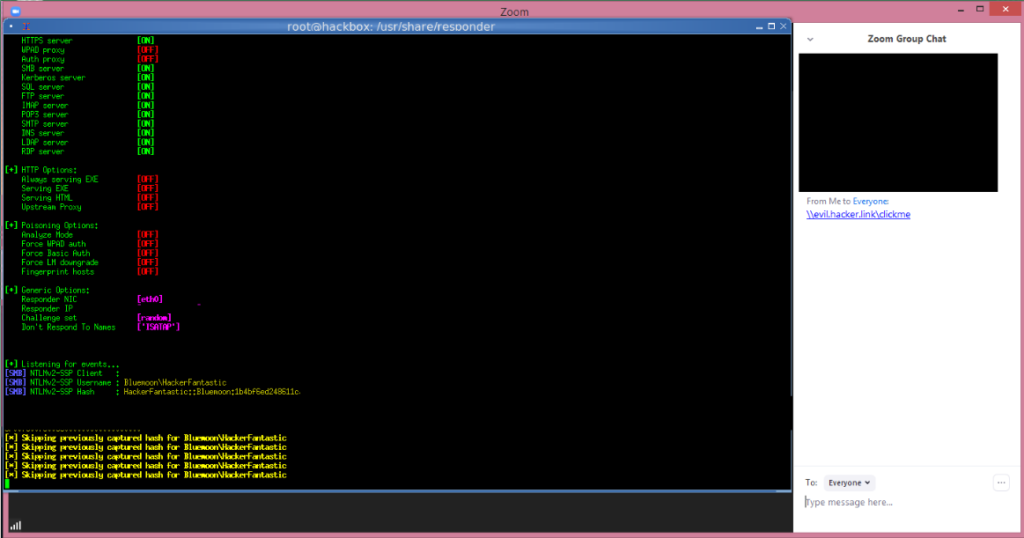
Security researchers tested the UNC injection in Zoom and was able to capture the NTLM password hashes being sent to a server hosting the clicked on share.
Is there a mitigation?
Waiting for a fix, there is a Group Policy that can be enabled that prevents your NTML credentials from automatically being sent to a remote server when clicking on a UNC link.
The policy is called 'Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers', needs to be set to "deny all" and can be found under the following path in the Group Policy Editor:
Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options -> Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers
Furthermore, this policy can be configured also using the Windows Registry, by creating this key:
RestrictSendingNTLMTraffic Registry value under the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\MSV1_0
and setting it to 2.