How to detect Cobalt Strike activities in memory forensics
A brief update on Cobalt Strike detection in forensics analysis, with a couple of new resources.
Some days ago I've published some informations about CobaltStrikeScan [1], a useful tool to identify Cobalt Strike beacons in processes memory, today l'd like to share a couple of resources useful to understand how detection works.
The first is a post by Riccardo Ancarani on F-Secure Labs, titled "Detecting Cobalt Strike Default Modules via Named Pipe Analysis" [2]. In this article, Riccardo explains how to spot in a compromized system activities of Cobal Strike beacons on Named and Anonymous Pipes.
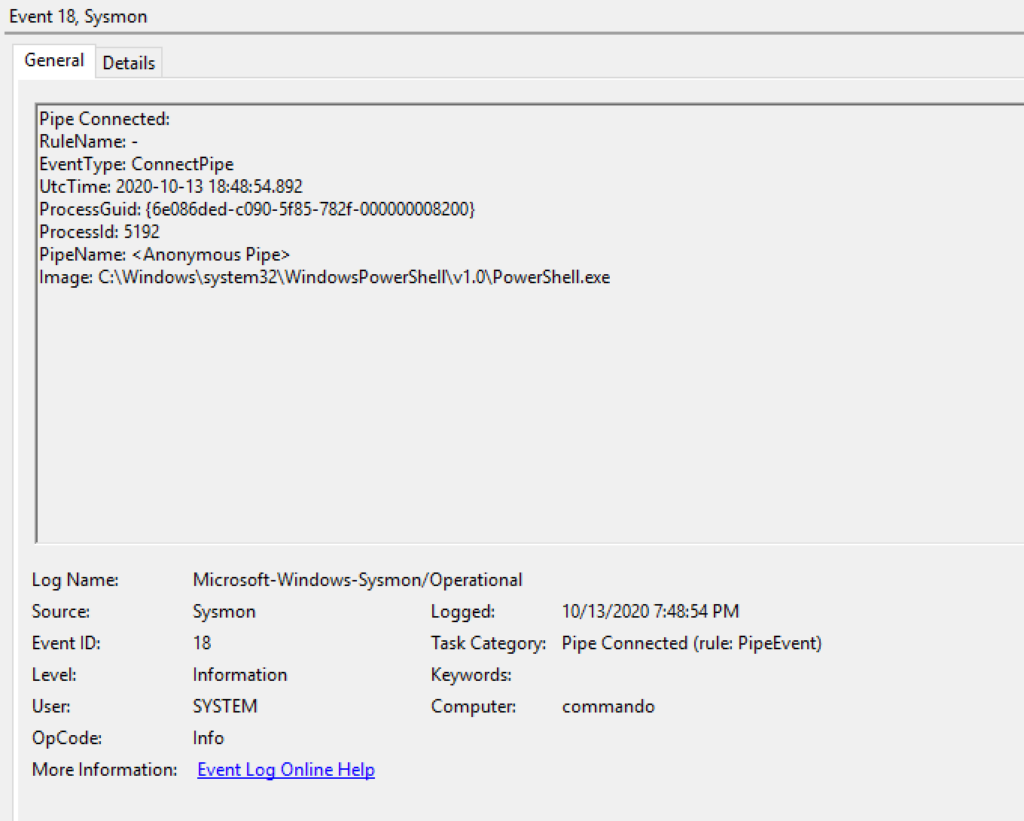
He also provides a sample YARA rule developed to identify those activities on processes memory:
rule cs_job_pipe
{
meta:
description = "Detects CobaltStrike Post Exploitation Named Pipes"
author = "Riccardo Ancarani & Jon Cave"
date = "2020-10-04"
strings:
$pipe = /\\\\\.\\pipe\\[0-9a-f]{7,10}/ ascii wide fullword
$guidPipe = /\\\\\.\\pipe\\[0-9a-f]{8}\-/ ascii wide
condition:
$pipe and not ($guidPipe)
}The second resource is a more complex papers, also mentioned by Riccardo in his article: "The art and science of detecting Cobalt Strike" [3], written by Nick Mavis for TALOS.
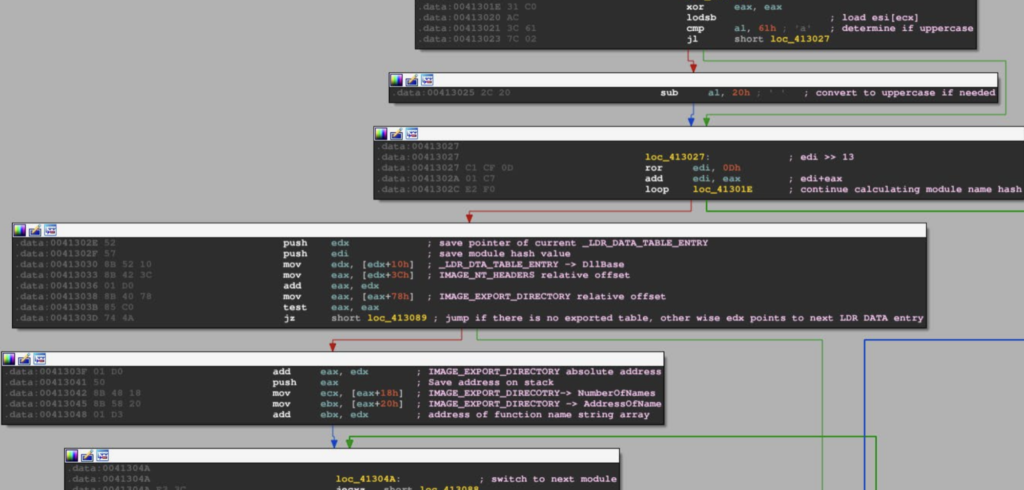
It is a more challenging reading, with several topics related to reverse engineering and memory analysis, with a special focus on beacon's injection techniques.
I hope it will be useful!